In our fast-paced digital world, the pressure is on to release new apps, features and enhancements as quickly and as often as possible. But how do you manage constant code changes without introducing security vulnerabilities?
And how do you address the elephant in the room that comes with increased usage of cloud apps in the wake of the disruption caused by COVID-19? New applications open new doors to new attacks. And those doors must be found and closed quickly.
This is where automated security testing comes in — the most popular of which are static application security testing (SAST) and dynamic application security testing (DAST). Each addresses different issues and has its own set of pros and cons, but both are aimed at increasing the speed, efficiency and coverage paths for testing applications as part of the software development lifecycle (SDLC).
Let’s take a closer look, and learn the advantages and disadvantages of using SAST and DAST and when to use one over the other — or even use both (which we recommend).
[ Learn about fuzz testing. | Want to see how it works or try 30-day free trial? ]
What is SAST?
Static application security testing (SAST) is a type of white-box testing used in earlier stages of software development to ensure secure coding practices and help developers detect vulnerabilities before the code is pushed into production. SAST solutions analyze applications from the inside out and run tests against static inputs and source code to check for flaws in the software before the code is compiled. This prevents hackers from exploiting vulnerable code and saves DevOps teams from having to fix problems after the application is deployed.
The use of SAST is recognized by OWASP as a key technique in finding weaknesses in source code and has many clear advantages including the ability to pinpoint the precise location of coding issues and find flaws early in development. Moreover, SAST can be automated and easily integrated into a continuous integration and continuous delivery (CI/CD) pipeline for delivering code changes frequently and reliably. All of this comes together as the most cost and time saving testing method and should be part of every application development process.
What is DAST?
Dynamic application security testing (DAST) is the opposite of SAST. Used later in the process, DAST tools do not have access to the source code, and test applications from the outside in, much like a hacker trying to break in. Because of this, DAST is often called behavioral testing or black-box testing (as well as fuzzing). DAST goes beyond SAST tools by looking at the whole environment of a running application, including how it’s used by end-users.
OWASP recommends using DAST tools for web application vulnerability testing, especially if those applications use open-source code which are prone to unknown vulnerabilities. It acts like a hacker scanning your application for vulnerabilities, but instead of exploiting them, DAST gives you the opportunity to remediate them before you promote the application to production.
Discovered vulnerabilities can then be used to locate issues in the architecture or design of the underlying code — improving its security as you make changes from DAST reports. It’s used to locate vulnerabilities across the entire attack surface, including API endpoints and web services, the physical infrastructure, as well as elements of a host system.
Overview of SAST vs DAST

SAST Pros and Cons
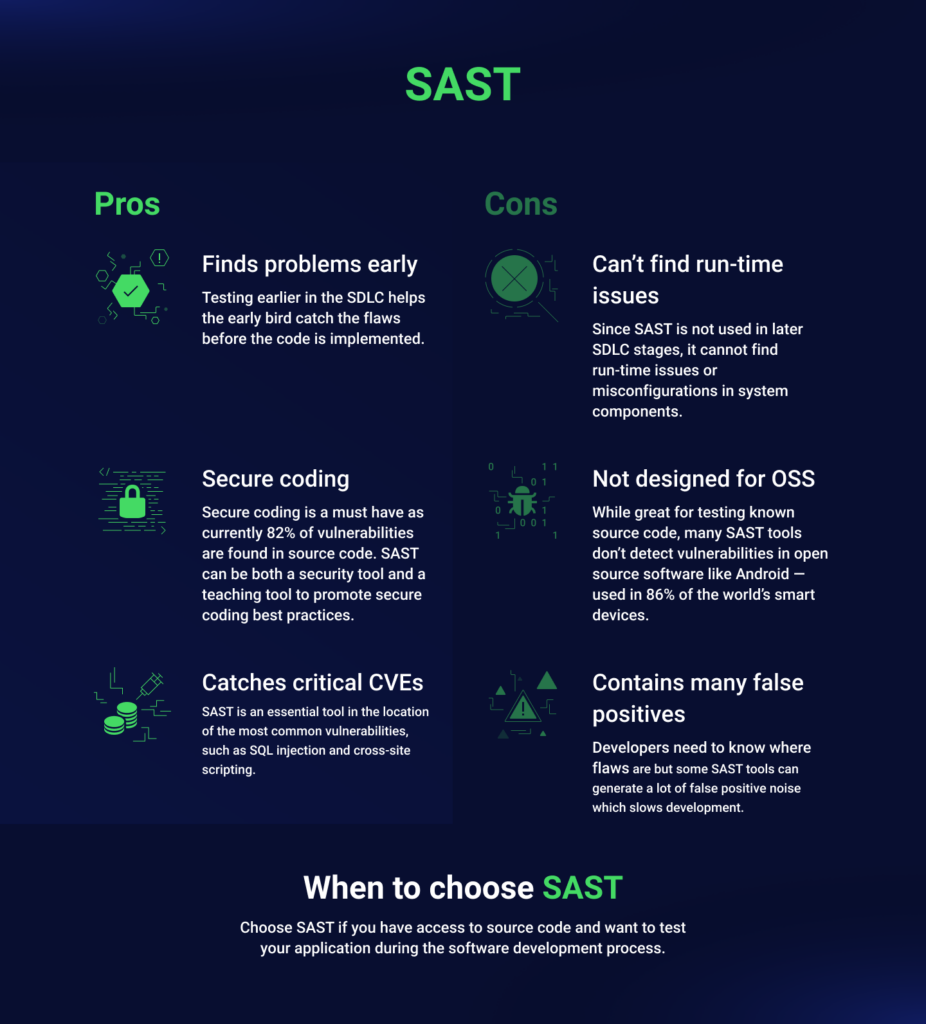
Using a SAST solution, your SDLC takes a “security first” approach to development. Developers get instant notifications as they generate logic and functionality into the codebase. SAST scanning identifies logic flaws that could be exploited. For example, unsanitized input can be used in a SQL injection or Cross-Site Scripting (XSS) attack. A SAST tool will identify functions that do not sanitize user-generated input and alert the developer to the flaw. The benefit is remediation of the vulnerability before it’s committed to the main branch of your codebase.
The disadvantage of SAST (and why it’s best to use both solutions) is that it can only identify a limited set of vulnerabilities. For example, a developer could sanitize user input but overlook a well-crafted SQL injection string. SAST may not find this oversight and allow the code to pass inspection.
Another disadvantage of a SAST tool is that it does not find misconfiguration errors. During deployment, servers are often configured to allow the software to run. A SAST only scans the developer’s code within their environment, so it does not identify vulnerabilities across your attack surface.
SAST pros and cons cheat sheet
DAST Pros and Cons
DAST solutions are a reactive approach to security, but they still have benefits that SAST tools don’t offer. The primary benefit is the ability to scan your entire attack surface across multiple servers, environments (e.g., cloud and on-premises), API endpoints, and other infrastructure. For example, you could have applications that work with your API endpoint that receive and deliver data. A DAST solution can be configured to scan endpoints for vulnerabilities in addition to the main application.
Although DAST solutions offer a more comprehensive scan of your environment, they have a few disadvantages. DAST solutions must be configured for your environment, so it requires a bit more knowledge in penetration testing and exploitations. If the environment is not well audited, you could miss an entry point and unknowingly have vulnerabilities.
A full scan of the environment could be overwhelming to developers. If they don’t know where the vulnerable code exists or understand reports, it could be difficult for developers to identify the functionality causing the issue. A DAST tool requires more knowledge of the OWASP Top 10 and what could happen in exploitation of the code.
Another concern with DAST tools is its limitations. DAST works with web-based applications, so you would need additional security support for software that cannot be scanned over the network (e.g., local desktop applications).
DAST pros and cons cheat sheet

SAST vs DAST: Which should you choose?
You could choose one or the other, but the most beneficial way to test your software is using both SAST and DAST. SAST runs while developers code, and DAST scans software after deployment to a testing environment. They both prevent vulnerabilities from being introduced to production, reducing your risk and likelihood of a data breach.
Using SAST and DAST together provides a 360-degree view of your application’s security. They both reduce the chance of introducing vulnerabilities to production, but each have their own methods of detection.
The best setup is to use both solutions, but let’s consider two scenarios where one would be more beneficial than the other.
Scenario 1: You have a team of developers writing code in one monolithic environment. Developers commit their changes to the main codebase as they finish their updates. The software is compiled monthly and promoted to a production environment on a scheduled date. Vulnerabilities aren’t found until much later, and developers must then go back and patch their vulnerable code. A SAST tool would be beneficial in this scenario, because it will scan code prior to being committed. Developers see the issue as they code, so they can fix it prior to the vulnerability ever being introduced into the main codebase.
Scenario 2: You have an efficient DevOps environment where automation is part of the SLDC. In your environment, you leverage containerization where deployment spans local and cloud platforms (e.g., Azure or Amazon Web Services). Developers code their changes, and then DevOps tools automatically compile code and generate a container where it’s deployed within minutes. This continuous integration and delivery (CI/CD) methodology speeds up deployment, but it expands your attack surface. A DAST tool would be beneficial in this scenario, because it will scan your entire attack surface and find configuration issues as well as vulnerable code in your production and testing environments.
A symbiotic approach to software security testing
Modern SAST and DAST tools assist operations and developers in understanding key security issues in your software. SAST, for example, can be automated and used to create reports that developers can rely on to quickly locate flaws in source code that can then be remediated. Real-time reports can be generated by SAST tools to provide on-the-fly feedback during the coding process. This prevents a cascade of flaws from being promoted during the software development lifecycle (SDLC). SAST can be used to combine DevOps and DevSecOps to provide a comprehensive view of an application’s vulnerabilities and give developers secure coding guidance.
Modern DAST tools also automate vulnerability testing and may incorporate ‘Fuzz Testing’ or ‘Black Box Fuzzing’. This technique tests for exploitable vulnerabilities in protocols, API interfaces, and other environmental variables. DAST tools can also be used with mobile device management (MDM) to find vulnerabilities in mobile apps across an expanded network, including remote users and users working with bring-your-own-access (BYOD) policies.
Modern software development and the DevOps process are essential for fast promotion of code and deployment of patches. However, this fast process also means that software vulnerabilities can be overlooked. Using automated SAST and DAST tools together provides a symbiotic DevSecOps/DevOps process built on actionable and effective testing and reporting. The merger of these two testing methodologies generates a more secure SDLC and reduces the overall chance that a promoted application will contain vulnerabilities that could result in a system breach.
Webinar: SAST vs DAST: partners or enemies
Watch this webcast to learn about:
- Application security challenges in the SDLC
- What is SAST?
- What is DAST?
- How to choose an AST tool
- The pros & cons of both SAST & DAST tools and where each fits in the DevSecOps pipeline
- Beyond Security’s automated application security testing tools: blackbox and whitebox testing
If you’d like to incorporate SAST or DAST into your SDLC or certify the security strength of your products, request a demo to learn how to get started.