We strive to make our products intuitive and efficient to use while at the same time offering the most comprehensive detection and response solutions on the market. Last year, with beSECURE 10, we added dozens of new powerful features including live, customizable dashboards, IT and OT convergence, agent scanning, credentials storage and new post scan integrations to increase security and reduce your mean time to respond (MTTR).
Live, customizable dashboards
Looking for real-time threat intelligence? You’re in the right place. We’ve moved beyond static dashboards and on to live, up-to-the-minute dashboards — with data pulled from the latest vulnerability scans and ongoing monitoring of your networks and assets.
Additionally, you can now create customized dashboards, widgets, asset groups, scan reports and more.
Frequently used charts and scorecards
Risk Distribution – for viewing the percentage of high, medium and low-risk vulnerabilities.
Quarterly/Monthly Trend – for viewing vulnerability trends over time
Bubble Graph – for viewing vulnerabilities according to CVSS score and affected hosts
Assets Trend – for viewing how many assets were tagged due to specified criteria
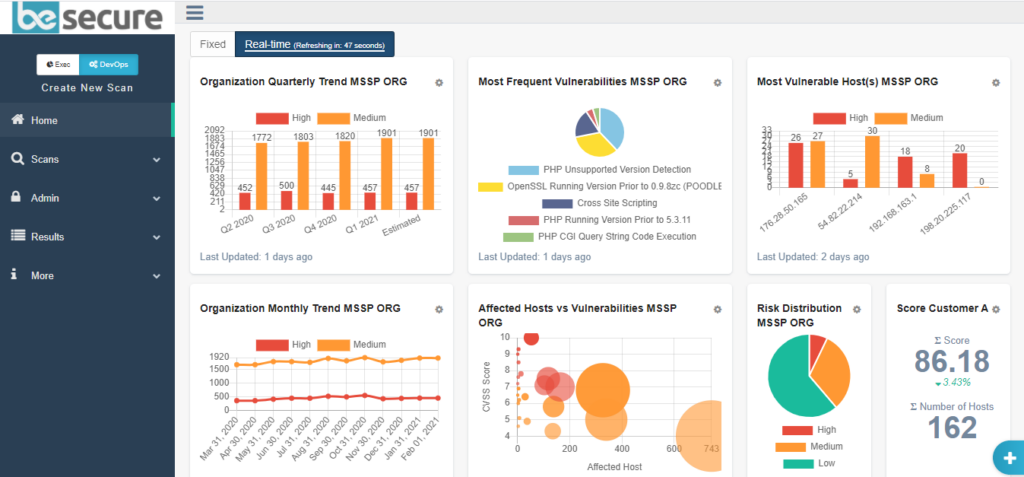
You can build personalized dashboard views after filtering data from a list of available options chosen to provide meaningful insights into risks affecting your business. Once you’ve finished building your dashboard, you can save your filters for future use.
Available dashboard filters
Category
- Quick Add
- Organization
- Scan
- Asset Group
Charts
- Affected Hosts vs Vulnerabilities
- Lowest Score Host(s)
- Most Frequent Vulnerabilities
- Most Frequent Vulnerability Type
- Most Vulnerable Host(s)
- Organization Monthly Trend
- Organization Quarterly Trend
- Persistent / New / Remediated Vulnerabilities
- Risk Distribution
Informational
- Preset Dashboard
- Major Vulnerabilities
- Major Categories
- Categories
- High / Medium Count
- Host Information
- Score
Organization
- Company
- Organizational groups and departments such as MSP clients
Get a 5-Minute Guided Tour of BeSECURE’s Current Features
Take a quick, step-by-step BeSECURE tour and see how VM can work for you.
Video: BeSECURE 10 – demo on demand
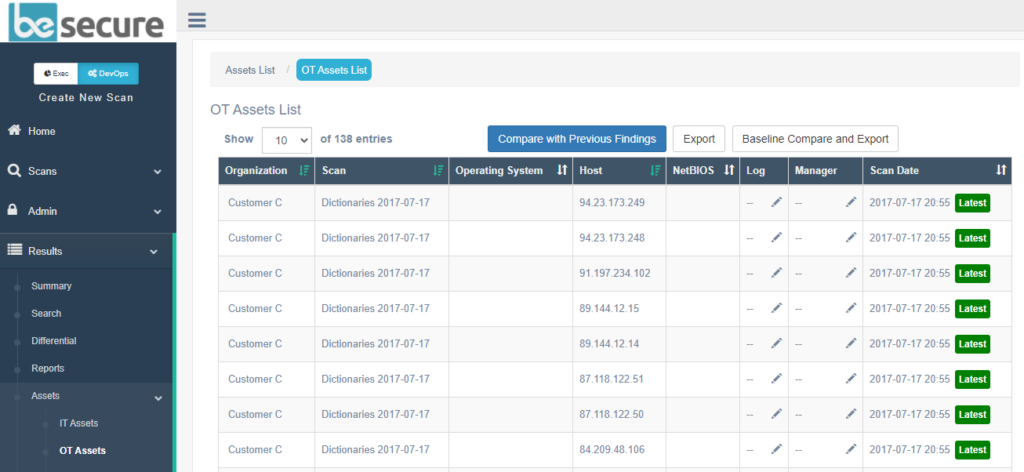
IT and OT assets management
We recently added OT scanning to our vulnerability management platform for unified IT, SCADA and ICS security. With beSECURE OT, security teams can monitor their entire infrastructure from a single pane of glass and protect operational technology (OT) from common exploits and weaknesses in SCADA systems.
The new OT assets view gives you critical information about your network assets including OS type, netBIOS name and IP address.
Learn about automated detection and network access control. Get a 30-day free trial. Contact one of our experienced Solution Engineers to find out how.
We also added agent-based scanning this year to give enterprises complete visibility across their networks and all connected endpoints including IoT, OT and BYOD assets. Users of agent-based scanning can now perform authenticated scans on endpoints not connected to the network – such as unmanaged devices used by remote employees – or on assets that are not “always on” such as desktops that may be turned off when the vulnerability scan runs.
Additional new features for assets management
Auto Tagging – for adding customized tags to your assets so you can view all related assets in one view and consolidate data needed to respond to alerts faster.
Port Overview – for identifying open ports that might be exposed to attackers and mitigating vulnerabilities targeting common ports
Device Collectors – for selecting a device collector that will automatically collect the devices (assigned to it) with no the need to manually enter hosts and IPs with the scan range into scans.
Credentials storage and post scan integrations
By enhancing our vulnerability management platform with third-party PAM (privileged access management) solutions, we have simplified credentialed scanning and privileged account security.
You’ll be able to retrieve or rotate login information anytime, anywhere without needing to update your credentials in the beSECURE platform. Recent PAM partners include: Thycotic and Wallix.
Other new integrators
Genians – for delivering cloud-based NAC (network access control) to forcibly quarantine vulnerable endpoints.
Ivanti – for quickly detecting vulnerabilities and instantly patching Windows and Linux machines as well as physical and virtual servers.
PagerDuty – for end-to-end vulnerability detection and incident response.
Portnox – for blocking vulnerable hosts from accessing selected networks via remote armed incident response.
Tufin – for increased visibility, control and incident response across heterogeneous networks.

Get a live demo
This version was all about improving efficiency and speed while continuing to manage your vulnerabilities with the accuracy you’ve come to rely on. Since we didn’t want to take all the fun away from our support and sales team, we only touched upon the biggest updates. To dig deeper into our latest version of beSECURE and learn about additional updates such as a new report scheduler and new CIS templates, please schedule a live demo.
If you are already a customer and need to reach support, please email: [email protected].